Enterprise Information Security Architecture
Definition: Enterprise Information Security Architecture (EISA) is the process of
instituting a complete information security solution to the architecture of an enterprise,
ensuring the security of business information at every point in the architecture.
The security of commercial data has always been a primary concern in business. Both for
ensuring the safety and integrity of customer data and protecting the competitive advantage
that comes with superior
business intelligence, information security is vital.
While security has always been a concern, it has become even more so since the introduction
of the Internet. Whereas in the past enterprises needed only to protect the flow of information
 within the business, today they must consider the threat from outside – from attacks on the
security of the corporate Intranet, for instance, or electronic data interchange (EDI) between
the enterprise, clients and suppliers. within the business, today they must consider the threat from outside – from attacks on the
security of the corporate Intranet, for instance, or electronic data interchange (EDI) between
the enterprise, clients and suppliers.
EISA is not, however, simply a matter of building a wall between the IT systems of an
enterprise and the outside world. Instead, the security architecture must align with the strategies
and objectives of the enterprise, taking into consideration the importance of the free flow of
information within an enterprise - and with partners, customers and suppliers.
Aspects of EISA
The goal of the Information Security Architecture
(developed by Gartner) is to align security strategies between three functional areas of an organization:
Business Architecture
Above all else, the security architecture must be aligned with the goals and objectives of the
enterprise. Without proper alignment there will be an inevitable disconnect between business
strategy and security.
To enable this alignment it is vital to accurately outline the business architecture in place to
achieve the objectives of the organization by asking several questions:
What does the enterprise do?
Who does it?
What information do they use to achieve their goals?
Where do they do it?
By answering these questions it becomes possible for the security architecture framers to develop a
comprehensive map of the strategies of the enterprise, along with a range of organizational charts
and business process maps.
Information Architecture
Using these plans, security architecture framers can understand the optimal flow of information within the
enterprise. What applications are used to achieve the objectives of the business? What data do these applications
require in order to achieve those objectives, and what integration methods are in place to enable the sharing of that information?
Only by understanding these technologies and processes can it be possible for the framers to develop a strategy
for ensuring the security of this data while allowing vital business processes to progress unimpeded.
Technology Architecture
Finally, it is necessary to study the technology architecture in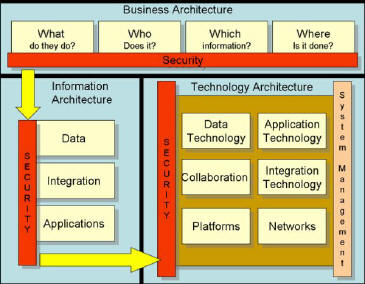 place to support these applications and
processes. The technology architecture of most enterprises is highly complex, involving a range of different
technologies running on different platforms, each relying on a range of heterogeneous legacy systems.
Ensuring the security of these technologies while allowing business processes sufficient access to
information can be a daunting task. place to support these applications and
processes. The technology architecture of most enterprises is highly complex, involving a range of different
technologies running on different platforms, each relying on a range of heterogeneous legacy systems.
Ensuring the security of these technologies while allowing business processes sufficient access to
information can be a daunting task.
In order to ensure the
security of data within this architecture it is necessary to build a map of
every piece of that architecture, and to understand how information moves between its components.
Primarily, it is vital to understand the hardware that supports business processes – the location and
purpose of servers, for instance, and the way in which computers access the information held on those servers.
Perhaps most importantly in the modern day is the need to build an Internet connectivity diagram for
the enterprise. Only by understanding the various connections between the information architecture and
the outside world is it possible to protect those connections.
In a Nutshell
Clearly, the process of developing a functional information security architecture is more complex than it may seem. Not only must the framers of such an architecture be aware of every piece of technology that exists within the business architecture, but they must also understand how and why all of these technologies interact with each other to achieve the objectives of the enterprise. Only once they have this understanding can they set about the task of developing best practices to ensure the security of information passing along these connections while optimizing the passage of information to protect the interests of the enterprise.
|
 within the business, today they must consider the threat from outside – from attacks on the
security of the corporate Intranet, for instance, or electronic data interchange (EDI) between
the enterprise, clients and suppliers.
within the business, today they must consider the threat from outside – from attacks on the
security of the corporate Intranet, for instance, or electronic data interchange (EDI) between
the enterprise, clients and suppliers.
 place to support these applications and
processes. The technology architecture of most enterprises is highly complex, involving a range of different
technologies running on different platforms, each relying on a range of heterogeneous legacy systems.
Ensuring the security of these technologies while allowing business processes sufficient access to
information can be a daunting task.
place to support these applications and
processes. The technology architecture of most enterprises is highly complex, involving a range of different
technologies running on different platforms, each relying on a range of heterogeneous legacy systems.
Ensuring the security of these technologies while allowing business processes sufficient access to
information can be a daunting task.