Internet SCSI
Definition: iSCSI or Internet SCSI is pronounced eye skuzzy and is an IP-based standard used
for linking data storage devices over a network and enabling the transfer of data by carrying
SCSI commands over IP networks.
iSCSI is a TCP/IP-based protocol which enables the transport protocol for SCSI which is
operational on top of the TCP. It offers a mechanism for capturing SCSI commands on an
IP network. It is a protocol for data storage systems that natively use TCP/IP. Packet
delivery with SCSI is different from that with IP. Packet delivery in IP is not in a fixed order.
Since iSCSI makes use of the ubiquitous Ethernet, it offers enormous potential for
low-cost centralization of storage.
With SCSI as a channel interface, the packets are delivered in a sequence and a
break in sequence can lead to data loss. Also, iSCSI requires a bulkier packet
head that contains additional information for speeding up packet assembly. The
delay/latency that occurs in data transfer over the Ethernet is one of the main
reasons holding back the commercial advance of iSCSI. That said, techniques like
the TCP Offload Engine (TOE) are proving useful in reducing overheads associated
with the TCP/IP protocol. High Ethernet speeds are encouraging organizations to
deploy gigabit and 10 gigabit networks.
The attraction of iSCSI lies in the advantages it offers. These include consolidation
of data storage systems;
backup of
data; efficient
server clusters; ease of replication
and recovery. IP storage enables the realization of capabilities such as QoS, improved
safety and SAN geographic distribution. Storage area systems with native iSCSI offer
advantages in terms of providing a single technology that connects
storage systems,
servers, and clients existing in a LAN, WAN,
SAN. Storage systems need not be in
geographic proximity to the applications.
With an iSCSI interface, it is possible to transfer data to the storage devices using
not only data carriers and communicators but also network cards on the client side. However,
the use of network cards can consume significant amounts of processor power on the client’s side. but also network cards on the client side. However,
the use of network cards can consume significant amounts of processor power on the client’s side.
iSCSI is a great way to access disk drives over a LAN. It eliminates the need to buy,
deploy, install, learn, manage, and upgrade a new networking infrastructure. Since disk
drives themselves do not have Ethernet connectivity, intelligent controllers are used to
act as iSCSI target devices so that the SCSI packets transferred through the GiGE cables
are converted into a language compatible with the disk drive. The controllers also cache
I/Os in the memory so that latencies inherent in the drive are masked.
Major components of iSCSI include:
• iSCSI Address and Naming Conventions.
• iSCSI Session Management.
• iSCSI Error Handling.
• iSCSI Security.
SCSI devices available in a network are identified through iSCSI nodes that are named
according to the rules adopted for naming internet nodes. An iSCSI name enables quick
identification of an iSCSI device regardless of its physical location.
Session management with iSCSI consists of two phases, a login phase and a full-feature
phase. The Fiber Channel Port Login process and the Login Phase of the iSCSI are identical.
The iSCSI protocol provides measures for handling errors because there is a high
probability of errors in delivering data over IP networks. The protocol also provides
security measures to protect data over networks susceptible to illegal access.
iSCSI security is a major concern with IT administrators because of the easily available
Ethernet operable devices. Best practices to ensure iSCSI security include segregating the
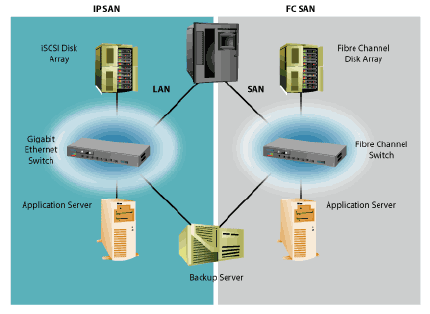
iSCSI SAN so that the iSCSI storage is not exposed to the open LAN. An iSCSI array should be
connected only to the
data storage servers and preferably a physically isolated iSCSI
SAN island should be created.
 The management interface should be secured to prevent unauthorized access from hackers.
This is particularly true with web-based configuration tools that can be accessed from
anywhere. Services such as DHCP, DNS, and WIN are superfluous on an iSCSI SAN and
should be disabled. Authentication such as CHAP and encryption such as IPSec should
be employed wherever required. The management interface should be secured to prevent unauthorized access from hackers.
This is particularly true with web-based configuration tools that can be accessed from
anywhere. Services such as DHCP, DNS, and WIN are superfluous on an iSCSI SAN and
should be disabled. Authentication such as CHAP and encryption such as IPSec should
be employed wherever required.
The evolution of iSCSI gathered momentum after it was approved as an industry
standard in 2003. At present, the majority of the deployments use software-based
iSCSI initiators and standard Ethernet NICs; however, there is an increase in the
demand for TCP offload enabled (TOE) enabled iSCSI adapters. TOE adapters help
manage high traffic storage environments.
Disk server software is available at different price points that cater to
environments of different sizes and the type of features needed. With this
approach, you pay only for what you use; this makes it possible to start with
the minimum software set required for your storage needs and then upgrade when
new features are required. An important feature that can be added later is the
Fibre Channel host connections alongside the iSCSI ports for higher, more
deterministic I/O performance required by larger hosts.
By including software-enabled disk servers in your iSCSI solution, you add to the
flexibility and performance of your set-up. You can choose from a range of hardware
platforms, price tiers, and extra features that may not be available from
purpose-built appliances or arrays.
|
 but also network cards on the client side. However,
the use of network cards can consume significant amounts of processor power on the client’s side.
but also network cards on the client side. However,
the use of network cards can consume significant amounts of processor power on the client’s side.
